
Boundless — Boundless Scalability
A Focus on Boundless's Structure and Features
1. Introduction
The Ethereum network maintains high security and decentralization through a structure where all nodes repeatedly perform identical computations. Consequently, as the number of nodes increases, the consensus process becomes more complex, synchronization overhead between nodes grows, and the network's throughput is constrained by the speed of the slowest node, resulting in reduced overall network efficiency.
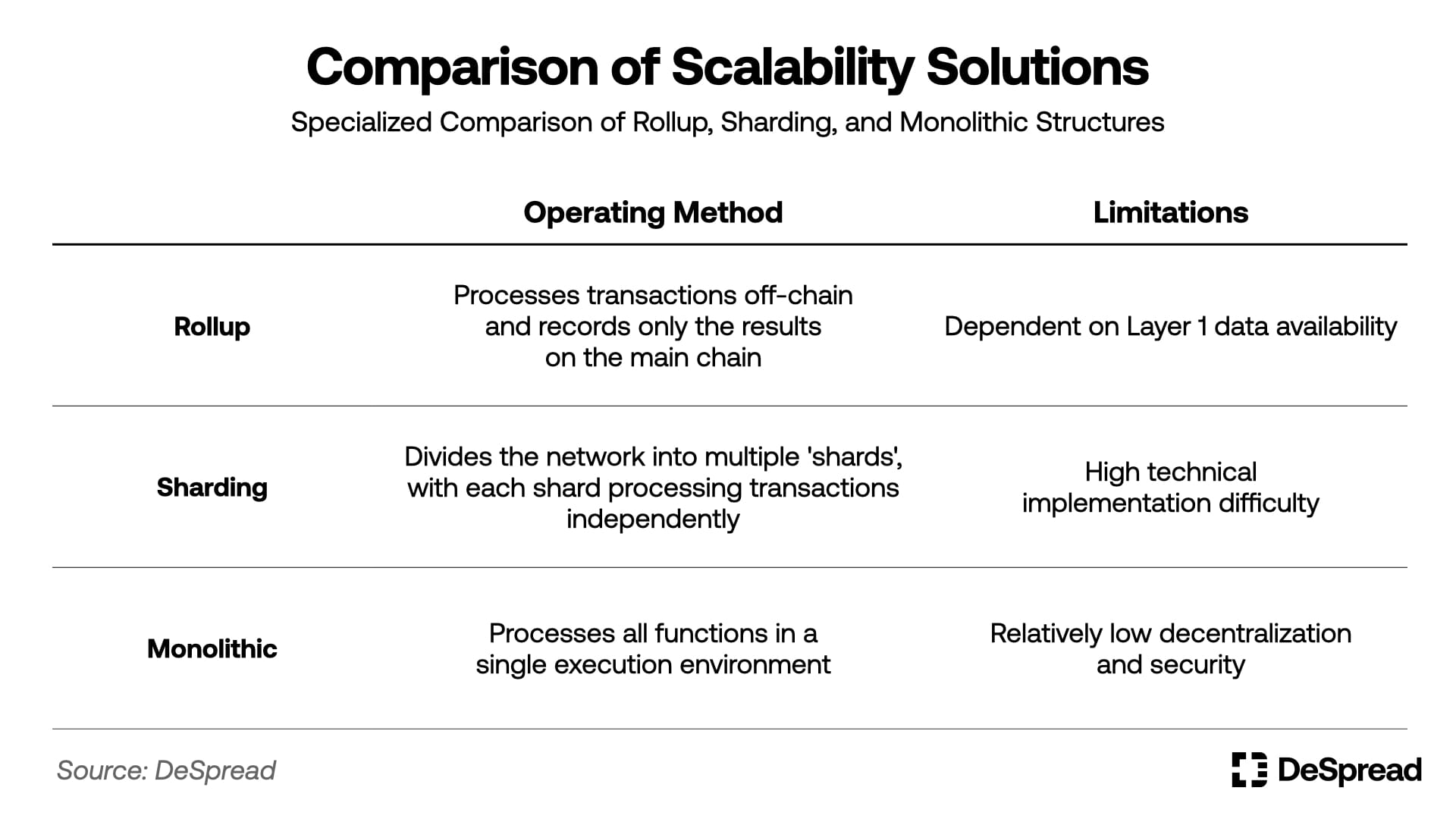
To address these limitations, the blockchain industry has pursued various approaches to overcome scalability challenges. Notable examples include Ethereum scaling solutions such as Rollups and Sharding, which aim to enhance scalability while preserving Ethereum's foundational architecture.
However, not all projects have followed the same path. Some blockchains, represented by Solana and Sui, have adopted monolithic architectures that prioritize high scalability even at the cost of some security and decentralization, securing their position in the industry by emphasizing fast transaction processing and improved user experience.
Ultimately, the blockchain ecosystem has developed along two parallel trajectories: 1) a path pursuing gradual expansion while maintaining security and decentralization, and 2) a path prioritizing immediate scalability. However, the former faces limitations in expansion speed, while the latter requires compromises in decentralization and security.
1.1 The Emergence of zkVM
In this context, zkVM (Zero-Knowledge Virtual Machine) is gaining attention as a new alternative.
zkVM is a technology that executes smart contract operations in a virtual machine capable of generating zero-knowledge proofs (ZK-Proofs) and guarantees the accuracy of results through compact proofs. This enables complex computations and large-scale data processing to be handled off-chain, while only result verification is performed on-chain, reducing chain load and securing scalability.
In essence, zkVM synthesizes the advantages and disadvantages of the scaling solutions described above, providing monolithic chain-level scalability while maintaining security and decentralization. Through this technology, the blockchain industry has gained a new development path that can simultaneously secure both security and scalability.
The advantages that blockchains can gain by adopting zkVM technology include:
- Predictable Verification Costs: Verification costs remain constant regardless of computation complexity, ensuring a stable and predictable cost structure even when handling applications with significantly increased complexity
- Harmony of Decentralization and Efficiency: While preserving blockchain's inherent strengths of decentralization and integrity, actual computations are processed off-chain, enhancing overall network efficiency
- High Security and Reliability: Users can receive proof that results were calculated accurately without directly verifying computation results, strengthening network reliability and enabling safe processing of complex calculations
- Extended Application Possibilities: As large-scale computations that were difficult to process on-chain become feasible, blockchain can expand into various application areas such as artificial intelligence, financial simulation, and large-scale data analysis
Thus, zkVM goes beyond simply improving blockchain performance; through the separation of computation and verification, it solves the scalability problems facing blockchain while preserving the advantages of decentralized networks, establishing a foundation for more active blockchain utilization in diverse fields such as AI, finance, and data analysis. However, as zkVM has only recently been developed and discussed, the technology has not yet reached the stage of widespread adoption across the industry.
At this juncture, Boundless aims to become a leader in zkVM by providing an environment that can be immediately applied to industrial settings, going beyond merely implementing zkVM.
2. Boundless: Breaking Through Scalability Limits
Boundless is a zero-knowledge verified computing layer developed by the RISC Zero team, designed as a zero-knowledge proof marketplace protocol that efficiently processes complex computations and enables secure verification. When blockchains or applications require high-performance computing, they can request it from the Boundless network, and anyone can become a participant, performing computations and submitting proofs to earn rewards.
The core mechanism of Boundless is the separation of computation and verification. Instead of all nodes on-chain repeatedly performing identical computations, specific nodes process complex computations off-chain and verify execution through zero-knowledge proofs. This allows the network to secure result reliability without requiring complete re-computation, becoming a key mechanism for solving blockchain scalability problems.
2.1. Boundless's zkVM
Boundless is built on the zkVM developed in-house by RISC Zero. The RISC Zero zkVM has a structure that can execute arbitrary programs using general-purpose RISC-V instructions and generate cryptographic receipts proving that execution was performed correctly.
Since the zkVM automatically handles complex zero-knowledge proof generation, developers using it can write zkVM-compatible programs and develop verifiable programs in familiar languages such as Rust and C++ without separate cryptographic knowledge.
Additionally, RISC Zero zkVM is a high-performance STARK-based proof system that can measure computational workload in RISC-V CPU cycle units, making it suitable for implementing Boundless's incentive mechanism, PoVW (Proof of Verifiable Work).
Furthermore, while Boundless currently uses RISC Zero zkVM as its default execution environment, it aims for universal design that is not dependent on specific proof systems. In fact, Boundless's roadmap includes plans to support other zkVM backends such as Succinct's SP1, zkSync's Boojum, and Jolt, allowing developers to utilize Boundless while creating applications in their familiar manner without being locked into specific development tools or environments.
In other words, Boundless adopted RISC Zero's zkVM based on these advantages, and it can be seen as having established a foundation that maximally utilizes versatility, performance, and development convenience while being able to evolve into a flexible platform encompassing various development tools and environments in the long term.
Let's now examine Boundless's architecture and operating mechanism in detail.
2.2. Boundless Protocol Architecture
Boundless consists of two main participants, App and Prover, and is composed of contracts and streams connecting these participants.
- App: An application that requests verification of specific computations (calculations) using the Boundless system
- Prover: An entity that actually performs computations requested by apps off-chain and generates cryptographic proofs demonstrating that computations were performed correctly
- Verifier Contract: A smart contract that verifies the cryptographic validity of proofs generated by provers on-chain, technically judging only the truth value (True/False) of proofs
- Market Contract: A core contract serving as the coordinator of the Boundless ecosystem, performing roles of proof intermediation, verification requests, and payment processing
- App Contract: An app-owned contract that receives final verification completion signals (and results) from the market contract and executes the application's next logic or stores final state on-chain using verified data
- Off-chain Order Stream: A communication component that broadcasts major off-chain data (requests/responses) such as app proof requests and prover auction bids
Boundless's verifier contract and market contract are deployed and operated on settlement-dedicated networks (Settlement Chains) such as Ethereum and Base. Additionally, app contracts deployed by application developers also operate based on these settlement-dedicated networks, receiving verified proofs and executing business logic.
In contrast, provers execute zkVM programs and generate proofs using their hardware off-chain, outside the settlement-dedicated layer, and receive rewards according to the PoVW mechanism when the correctness of generated proofs is verified.
Furthermore, while apps can submit computation requests directly to the market contract through on-chain transactions, when censorship resistance is less critical, they can exchange proof requests off-chain through order streams.
Thus, Boundless has a structure that maximizes efficiency through a hybrid design where verification and payment processes requiring trust and security are handled on-chain, while computation-intensive proof generation is performed off-chain.
2.2.1. Detailed Operating Process
Boundless's operating process proceeds through six stages from application proof requests to final result utilization.
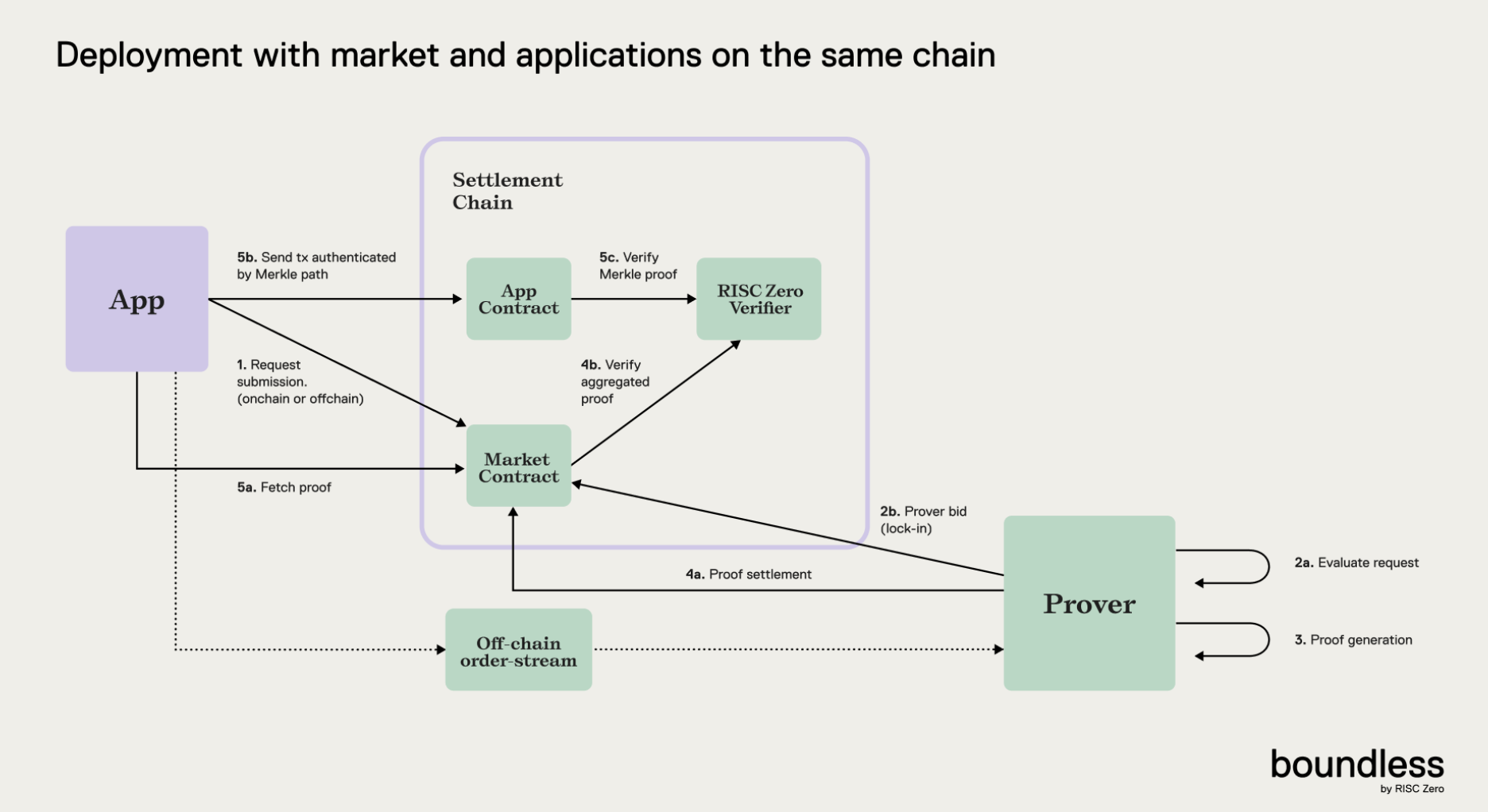
- Proof Request Submission: App proof requests can be submitted on-chain (direct transaction to market contract) or off-chain (order stream broadcast). Requests include information about the program to execute, input data, and prover auction conditions
- Prover Bidding and Lock: When a request is broadcast, a reverse Dutch auction begins. The price starts at minimum and rises to maximum over time, and provers can bid at their desired time point, depositing collateral and locking the request
- Proof Generation: The prover who executed the lock runs the zkVM program with their hardware off-chain and generates a proof. For efficiency, multiple requests are bundled into batches to generate a Merkle tree-structured aggregated proof
- Proof Submission and Verification: The prover submits the aggregated proof to the market contract, which forwards it to the verifier contract for verification. When verification succeeds, the prover receives rewards and collateral is returned
- Proof Receipt and Re-verification: The app detects the completion event, retrieves the Merkle inclusion proof, and transmits it to the app contract. The app contract independently re-verifies the proof through the verifier contract to confirm result accuracy
- Result Utilization: When verification succeeds, the app contract executes business logic based on the proven results. Results of complex computations performed off-chain can be safely utilized on-chain without re-computation by all nodes
Through this method, Boundless has a structure that realizes reliable computation execution, transparent verification, and automated settlement even in a decentralized environment.
3. Current Status and Key Collaboration Cases
On September 15, 2024, Boundless officially launched based on the Base chain and conducted a $ZKC token airdrop for incentivized testnet participants who had been participating since July. Boundless subsequently opened staking functionality, providing additional utility to $ZKC holders.
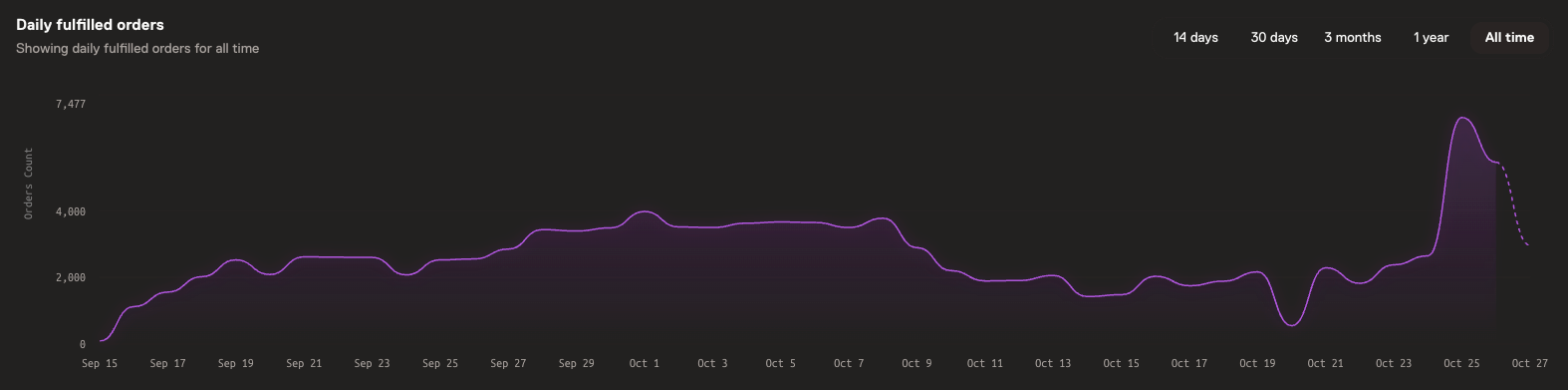
Since launch through the writing date of October 27, cumulative proof requests executed through Boundless total 1.4M, showing approximately double the performance compared to Succinct, a competing protocol that launched earlier than Boundless.
The Boundless team is actively pursuing collaborations with other protocols to attract more users and expand the ecosystem, with key ongoing collaboration cases as follows:
3.1. EigenLayer: AVS Slashing Verification Improvement
The restaking protocol EigenLayer plans to efficiently handle slashing verification logic for AVS (Actively Validated Services) operators using Boundless.
Boundless's zkVM-based prover network periodically collects and calculates staking balance information from various sources including Ethereum, summarizing results as Merkle tree roots. On-chain verification contracts confirm submitted proofs to understand each validator's stake status and execute slashing at low cost when rule violations are detected.
In this process, all complex computations are performed off-chain, and only simple zero-knowledge proofs are submitted on-chain. Computations that would cost tens of millions of gas if executed directly in Solidity are replaced by a single proof verification, expected to reduce gas costs by up to 99.9%. Boundless is currently proceeding with integration with EigenLayer.
3.2. Celestia: Data Availability (DA) Proof
Celestia, a modular data availability layer, collaborated with RISC Zero to develop Blobstream Zero, a zkVM-based cross-chain messaging protocol.
In Blobstream Zero, Boundless provers prove off-chain that all transaction data within Celestia blocks is actually stored and maintained in the network, submitting this as compressed zero-knowledge proofs to other chains. Consequently, contracts on other chains can trust Celestia's data availability by simply verifying this small proof.
In particular, since Boundless zkVM can consolidate multiple DA verification tasks into a single proof, rollups or applications using Celestia as their DA layer can perform low-cost, high-trust data availability verification without directly storing entire data or complex sampling procedures.
Blobstream Zero is currently developed in open-source public form and is applied in the mainnet environment.
4. Competitive Environment and Differentiation Factors
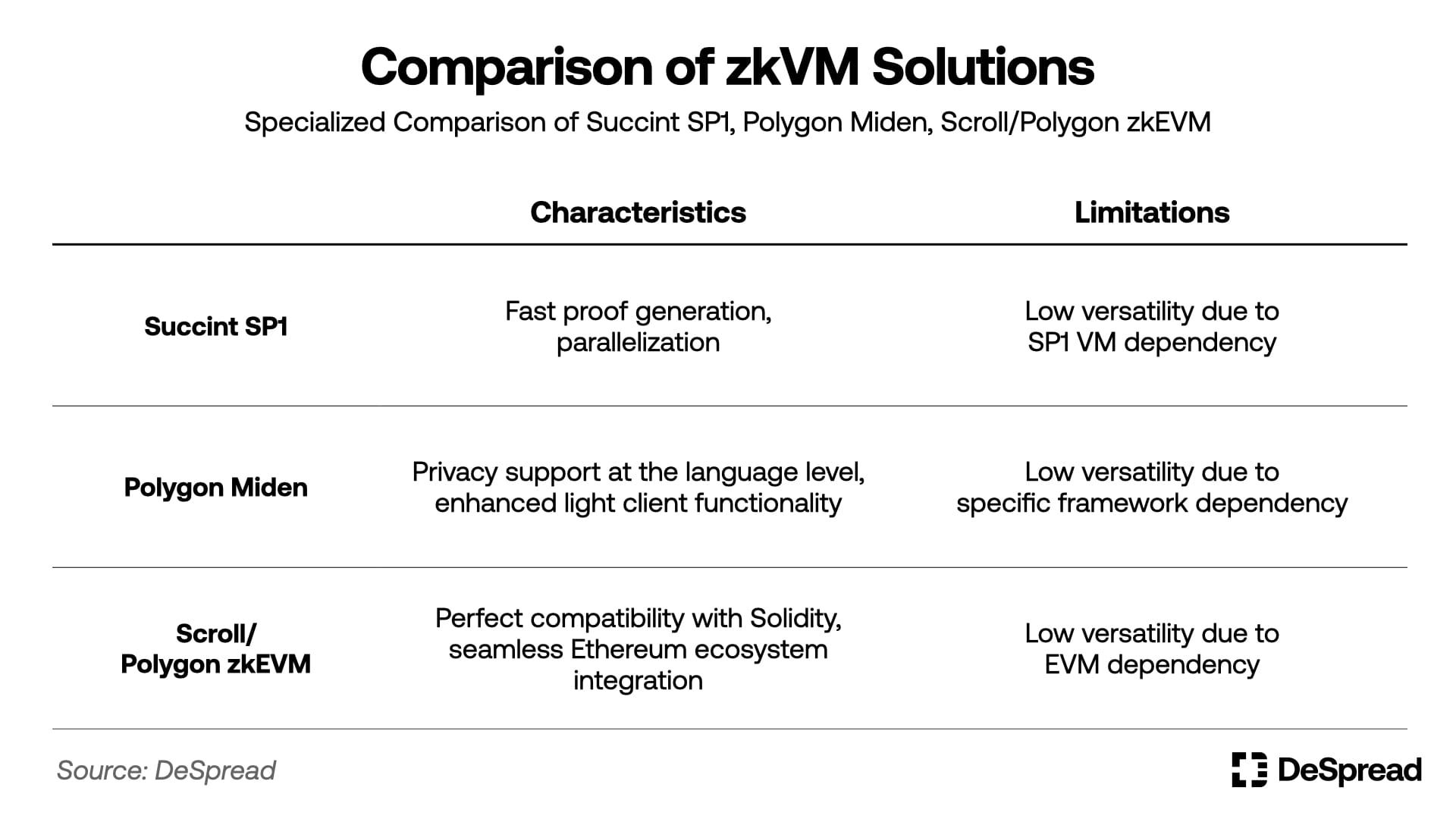
Currently, the zkVM field includes several competitors such as Succinct's SP1, Polygon's Miden, and Scroll's zkEVM, with each project placing different strategic focuses for the success of their respective virtual machines.
Boundless has three core distinguishing features compared to other competing projects:
- VM-Agnostic (Versatility): Provides a technical foundation that can perform computations and generate proofs regardless of VM (EVM, RISC-V, etc.) or blockchain environment
- Ecosystem Scalability: Builds an economic ecosystem where anyone can participate as a prover, perform computations, and receive rewards
- Open Marketplace: Designed so that the network is maintained and grows through voluntary motivation of market participants rather than subsidies from central entities, through a decentralized proof marketplace structure
In particular, it is encouraging that Boundless has built a virtuous cycle structure by applying the economic incentive model, which is the core driving force of the blockchain industry, to the proof generation market, where participants gain rewards for providing computational resources and the network achieves sustainable scalability and decentralization.
Through this, Boundless can be seen as executing a strategy to "create an economic network where anyone can supply and consume zero-knowledge proofs," going beyond the technical competition of "how fast is my zkVM." This approach positions Boundless as 'ZK Proof-as-a-Service'—a versatile and scalable infrastructure not confined to specific use cases.
5. Conclusion
Boundless presents a fundamental solution to blockchain scalability problems. By utilizing RISC Zero's zkVM technology to process complex computations off-chain and efficiently verify only result accuracy on-chain, it overcomes the structural limitations of existing blockchain networks like Ethereum.
Boundless's greatest differentiator is that it has built the zero-knowledge proof generation process into a decentralized proof market, going beyond simply improving technical performance. This system, where anyone can participate as a prover, provide computational resources, and receive compensation, establishes a sustainable foundation where the network can autonomously grow and be maintained without subsidies from central entities.
However, while Boundless has a vision to expand into various industrial fields such as AI, financial simulation, and large-scale data analysis, the demand and collaboration cases confirmed to date are concentrated within the blockchain industry. Therefore, it is necessary to closely monitor mainnet operation performance and proof of technical reliability regarding whether Boundless can actually expand beyond blockchain into traditional industry sectors.
If Boundless successfully addresses these challenges and is adopted across various industrial fields beyond blockchain, it is expected to become a major case demonstrating the potential for zkVM technology to establish itself as general-purpose computing infrastructure, while showing that verifiable computing provides practical value across industries.
References
- Bondless Explorer
- Celestia Docs
- Boundless Docs
- Boundless Blog, Scaling EigenLayer's Security
- Fenbushi Capital, Benchmarking zkVMs: Current State and Prospects
- Yunjeong Heo, Exploring the Landscape of zkVMs
- twi, RISC-V, zkVM 그리고 succinct